By default, Invantive UniversalSQL requires all database connections to apply encryption by TLS (Transport Layer Security). This makes it quite hard for prying eyes along the transport route to see and/or alter your data, similar to HTTPS.
This requirement holds for both on-premises as online use.
However, some cloud platforms and/or hosting parties did not or only partially implement TLS for database connections.
Online
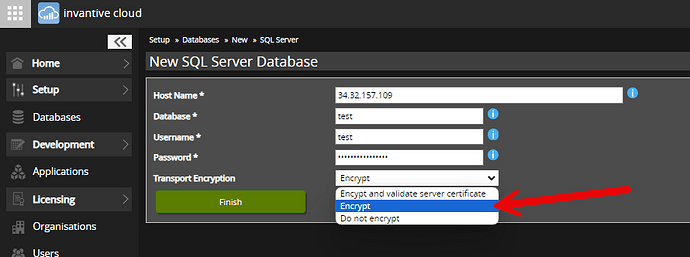
For online use, Invantive Cloud now allows reduction of TLS on creation of a database for SQL Server, PostgreSQL and MySQL. To disable certifate validation, use “Encrypt” instead of “Encrypt and validate server certificate” as shown below:
Transport encryption can even be disabled completely by selecting “Do not encrypt”.
On-premises
For on-premises use, the following articles describes how to disable TLS:
Warning
The use of unsecured data connections makes it more likely that third parties controling devices along your data path (such as routers) can access and/or change the data transported. Please consult your local security officer for advice.